In section one we learned about operating systems and their primary functions. There are two sets of functions which are user functions and system functions. User functions include the user interface (UI), file system management, program execution, input output (I/O) operations and control, error detection, and communications management. The system functions of the OS are resource allocation, protection and security, and accounting. The UI is what the user visually sees and interacts with. The UI is displayed on a monitor and manipulated with a keyboard and mouse, which are part of the I/O portion of the operating system. The file management system of the operating system allows users to create and rename some files. (Silberschatz et al., 2014) The developer of the operating system or a System Administrator will have control of who can access certain files and programs. This is called the access matrix. Program execution is somewhat self-explanatory in operating systems as it gives them the ability to start and stop programs. During starting or stopping these programs there will occasionally be errors. These errors are detected by the error detection system.

In section two we discussed Processes, process state, control blocks, single and multi-threaded motivations, and the critical section problem. A process is the unit of work in a modern timesharing system, and it’s also described as a program in execution. The process includes the current activity, and the contents of the processors register. It also includes a process stack that contains temporary data, a data section to contain global variables, and it may also include a heap which is described as memory allocated during the process runtime. (Silberschatz et al., 2014) The process state is the current activity of the process. The different states of the process are new, running, waiting, ready and terminated. Only one of these processes can be running on any processor at any one time. Many processes can be ready and waiting, but not running. The different states of processes are new, running, waiting, ready and terminated when the process completes.
Threads were created to “provide a way to improve application performance through parallelism. Threads represent a software approach to improving the performance of the operating system.” (TutorialsPoint, 2021) A single thread completes a single task, so multiple threading is required in complex computer systems because many programs are executing at the same time. Multithreading although more efficient, more complications arise due to the complexity. The most important of which is the critical section of the processes. The critical section of a process requires the design of a protocol that all of the processes can use to cooperate with one another, and each process must request permission to enter its own critical section. The section of code that implements this request would be the entry section. It requests to enter the critical section and may be followed by an exit code. It is important to make sure that only one process is in the critical section at a time. If multiple processes enter the critical section at once it creates a race condition.

Section 3 was dedicated to the memory management in the operating system. The main purposes of memory management system are speed and efficiency. This is accomplished by optimized memory allocation between logical and physical organization. The objectives and functions of memory management are to allocate and de-allocate memory before and after a process, minimize fragmentation issues, keep track of used memory space by processes, proper utilization of memory, and to maintain data integrity during process execution. (Geeksforgeeks, 2023) The memory management unit, or MMU, is responsible for the assignment of memory space to a specific process. The MMU utilizes logical and physical addresses. The physical address space is an address that is seen by the memory unit, also known as the real address. Virtual memory is a technique that allows the execution of processes that are not completely in memory. Virtual memory allows programs to be larger than the physical memory. Virtual memory can execute a program that is only partially in physical memory. This allows more programs to run at the same time. Virtual memory is stored in a virtual address space and is accessible as if it were a physical address. The MMU is used to translate virtual addresses to physical addresses in the main memory which enables a process to use more space than exists in primary storage.

In Section 4 file management systems and the supported operations, mass storage and input output devices (I/O) were discussed. The main purpose of the file management system is to manage files on a computer. The file management system is responsible for creating, editing, erasing, and organizing files. This system manages different folders that are called directories. These directories keep files organized and different directory structures are used to achieve this. Some of the things performed by a directory are searching for a file, creating a file, deleting a file, rename a file, and to traverse the file system. Some of the different directories are a single level directory, a two-level directory, tree structured directory, the acyclic-graph directory, and the general graph directory.

Input-Output or I/O devices are used for data input, and output. “The role of the operating system in computer I/O is to manage and control I/O operations and I/O devices.” (Silberschatz et al., 2014) Common input devices are keyboards, mouse, webcam, microphone, trackpad, and stylus. Common output devices are monitors, speakers, headphones, and printers. Input output interfaces interpret the communications between different peripheral devices. This communication between hardware and software makes I/O devices operate properly. These interfaces are sometimes called drivers.
The final Section, Section 5, discussed the goals and principles of domain- and language-based protection in a modern computer system and how security is used to protect programs, systems, and networks from threats. The goals of domain and language-based protection are to prevent malicious activity by users or programs on a computer system. Domain based protection specifies the resources that processes may access, and each domain contains a set of objects and the different types of operations that may be utilized on said object. A domain is basically a collection of access rights. It dictates which operations a process can perform. The language-based protection is the protection type that allows for user defined functions. It allows system administrators to allow access or deny access to users or objects. this protection type allows more flexibility for application designers, which helps guard application subsystems against tampering. (Silberschatz et al., 2014)
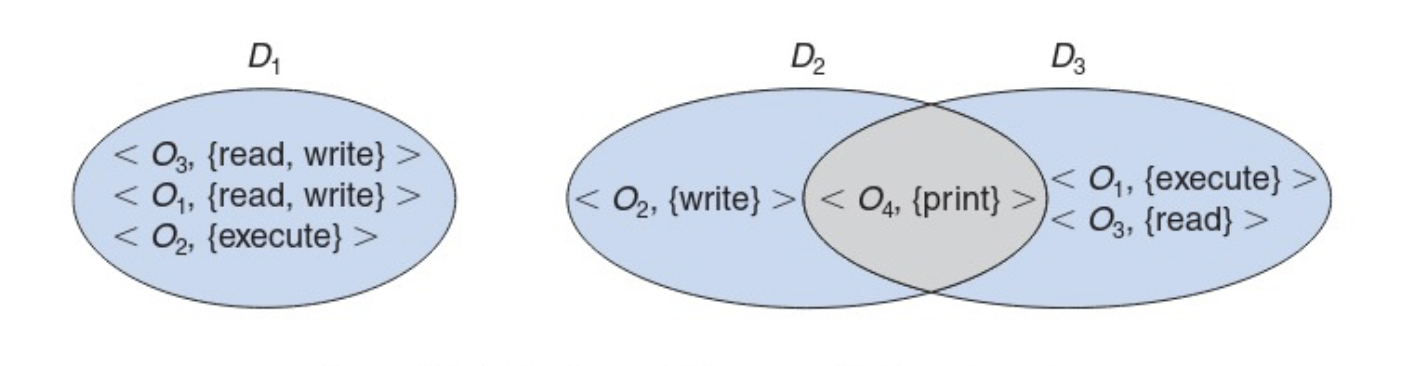
In the figure below there are three domains and there are four objects. The print object is shared by domain two and domain 3. Domain one is the only domain that can read and write to object one, yet domain 3 can execute on object one. This is an example of how domains are granted access to different objects.
The Figure below is an access matrix that is like the other figure as it represents domains and objects. If a process is executing on domain 3 it can read files on object F2 and execute on object F3. Domain D4 has the same privileges as D1 but can also write in addition to read. Only domain D2 can print.

Security is accomplished using four different levels of security measures. these four levels are physical, human, OS, and network. The physical level refers to the actual physical security of the device, as in where it is stored and how it is kept. The human level is in reference to humans either maliciously or unintentionally compromising systems. Humans can be bribed or tricked via social engineering attacks, or phishing. The third level which is the OS level is in reference to the operating systems need to protect itself from accidental or intentional security breaches, faulty processes. The last level of security is network security. Networks must be secure to prevent the loss or theft of data.
The further understanding that this course gave me about how an operating system functions is something I will need to eventually work in the cybersecurity career field. Much of these concepts and processes are unfamiliar to me. Expanding my understanding of how the operating system processes inputs, provides protection, and manages memory and files will be very helpful.
References:
1. GeeksforGeeks. (2023, January 9). Memory management in operating system. GeeksforGeeks. Retrieved February 16, 2023, from https://www.geeksforgeeks.org/memory-management-in-operating-system/
2. Silberschatz, A., Galvin, P. B., & Gagne, G. (2014). Operating system concepts essentials (2nd ed.). Retrieved from https://redshelf.com/
3. TutorialsPoint. (2021, July 28). Operating system - multi-threading. TutorialsPoint. Retrieved February 12, 2023, from https://www.tutorialspoint.com/operating_system/os_multi_threading.htm